Home / Our Products /
A split-second decision by an employee can have major consequences on an organisations security.
As an authorised Redflags® partner, Morgan Cyber Solutions provide the tools to educate and change cybersecurity behaviours. By deploying real time nudges in live scenarios, we divert your people away from high-risk activities and deliver measurable reductions in operational risk.
Prompt 2 Protect is all about delivering the right security training at the right moment.
Build a strong security culture to tackle both social engineering attacks and bad habit creep within your teams. In the below examples, Prompt 2 Protect steps in, providing gentle nudges to the user to guide good behaviour at critical moments:

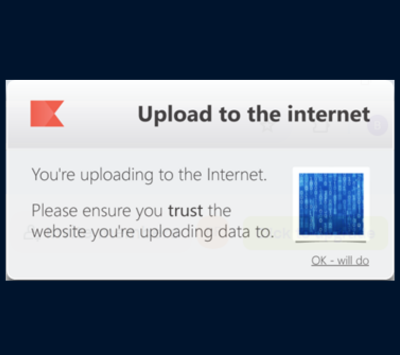

Prompt 2 Protect is the always on security ally, unobtrusively watching scenarios that could trigger potentially risky actions before engaging with users at the right moment.
Continuous training that takes place in the real world. Swap or enhance traditional point in time cybersecurity training with a modern approach rooted in behavioural science and proven to deliver measurable behaviour change.
Unrivalled training coverage. From reminding users to lock a screen when they walk away, to gently nudging them to verify that external request, or to report a suspected phishing email. Prompt 2 Protect is unique in regard to the breadth of its training.
Easy to measure effectiveness. With Prompt 2 Protect, you not only reduce bad security behaviors, you can prove effectiveness too. Use the advanced reporting tools to view engagement metrics and insights into your training to help you understand patterns and identify higher risk users.
Morgan Cyber are here to support you at every step on your journey to implementing Prompt 2 Protect. We will source the licenses you require and run training sessions for your advocates to help them get the most out of the tools available in the platform. If you have any questions at any point, we are just a phone call away.